End-to-end encryption is designed to protect your data, across different systems, everywhere it goes, and at any time.
End-to-end encryption is designed to protect your data, across different systems, everywhere it goes and at any time. In today’s ever evolving data driven world, data flows through multiple workflows and user flows.
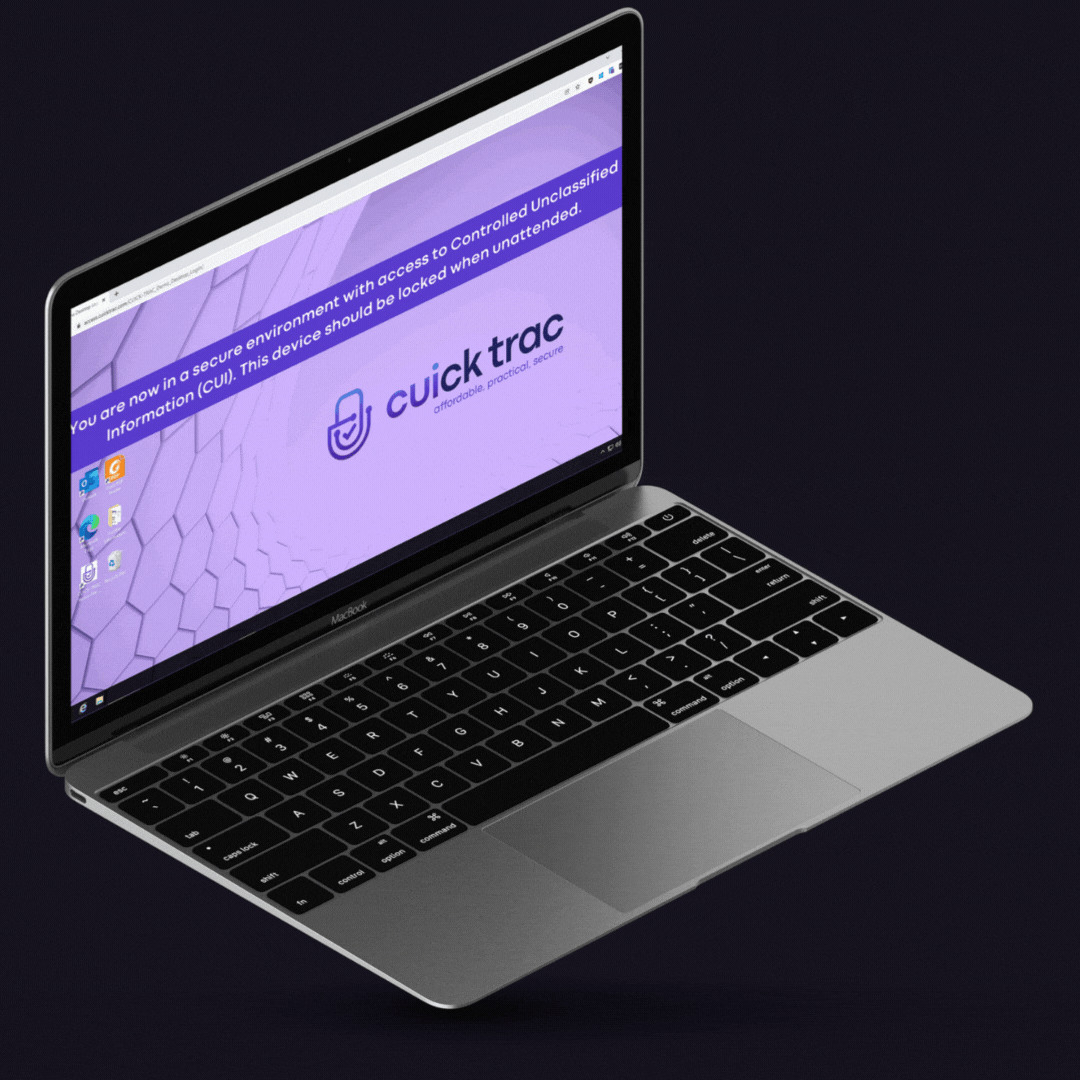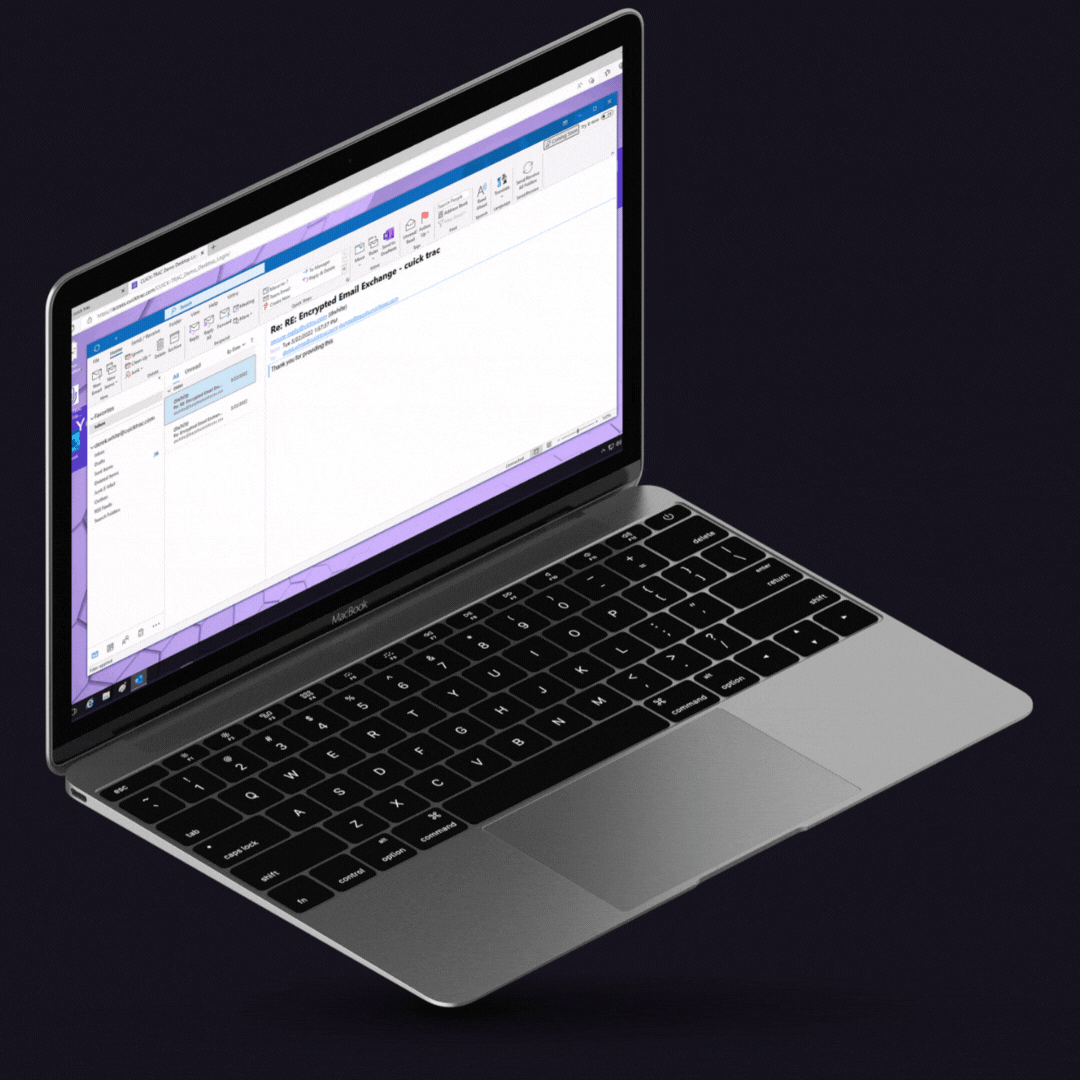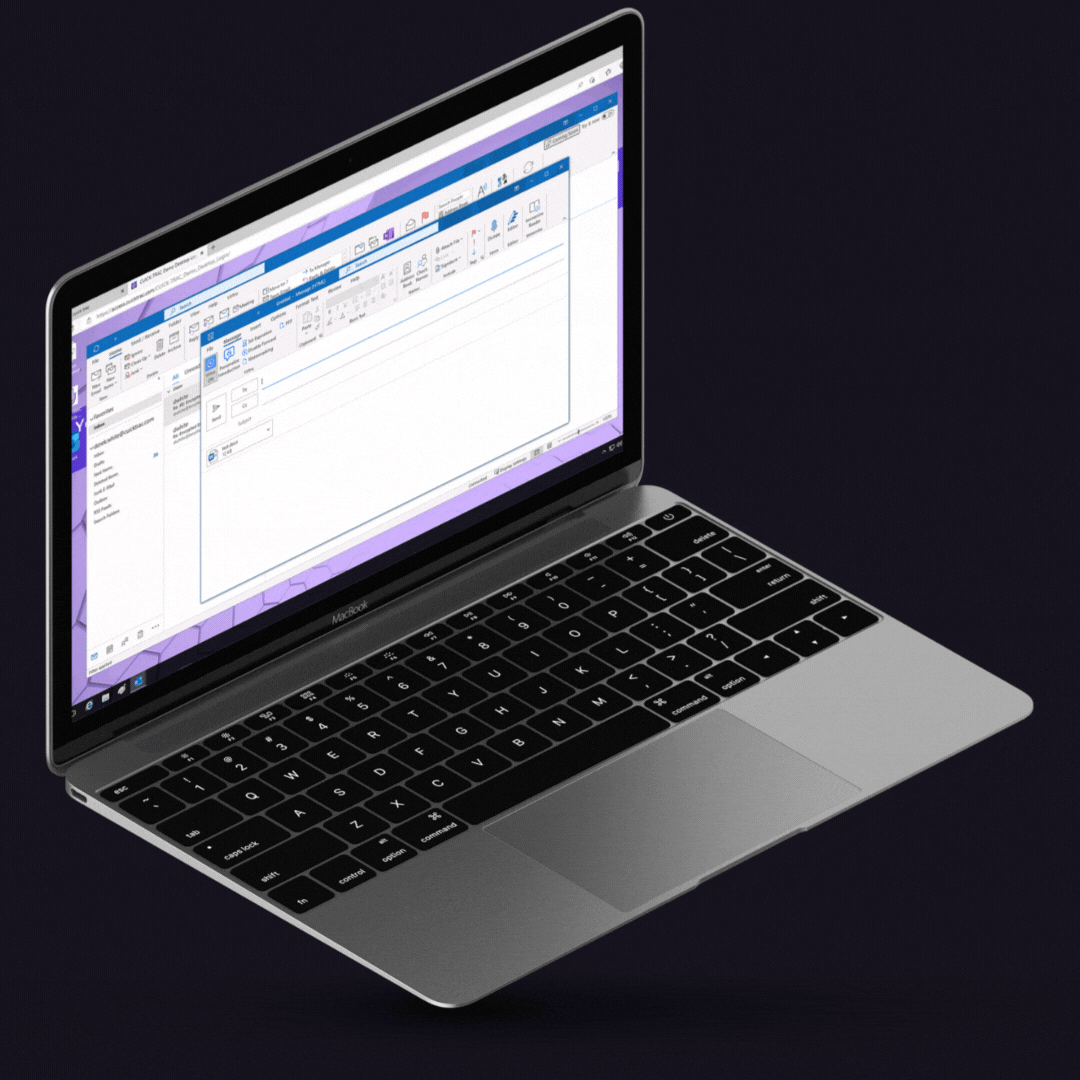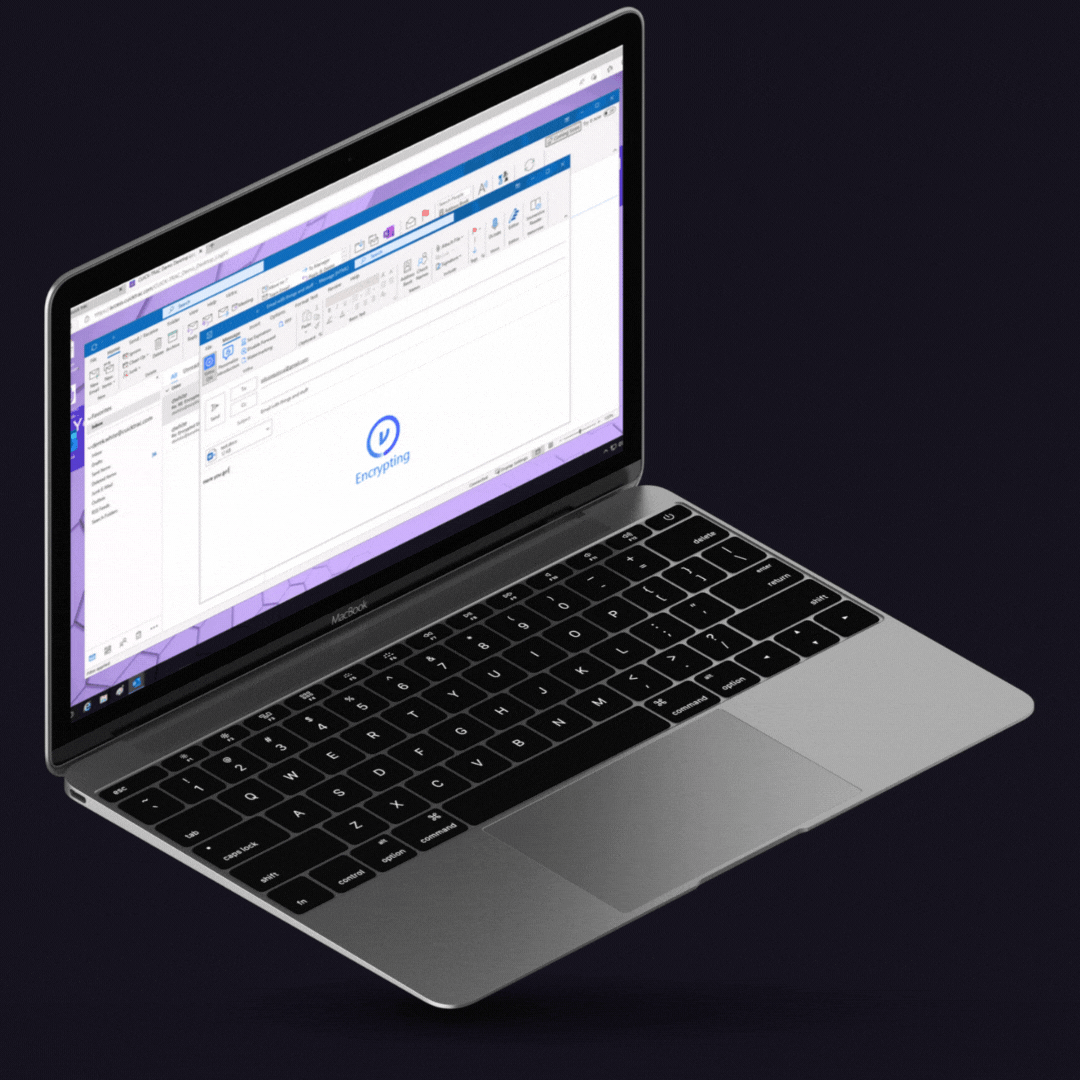
Now that data is the most valuable resource on the planet, it needs to be protected when it’s shared, received or stored. Some data is more sensitive than others, and therefore needs more secure methods to keeping it away from the wrong hands (and eyes). When it comes to DFARS, NIST 800-171 and CMMC, the requirements around protecting CUI are crucial to securing the DoD supply chain.
Protect CUI stored and shared via Gmail and Outlook from access by unauthorized users.
Share protected email and encrypted files containing CUI internally and with external primes, subcontractors, agencies, and other mission partners.
Support remote workers and distributed teams throughout defense supply chain collaboration workflows.
Boost user adoption with easy-to-use protections, seamless recipient access, and a quick installation process that gets users up and running in minutes.
The Cuick Trac enclave includes seamless end-to-end email and file encryption streamlines your preparations for CMMC.
Cuick Trac covers several CMMC practices and processes and NIST security requirements that protect CUI within email and files from unauthorized access throughout its lifecycle.
Complement user protections with DLP rules that automatically enforce CUI protections.
Enable seamless access for recipients and supply chain collaborators via the Secure Reader, without requiring new accounts, passwords, enabling innovation and growth.
Enable secure sharing between primes, subcontractors, and mission partners by implementing CMMC practices for Access Control, Audit and Accountability, Identification and Authentication, Media Protection, and Systems and Communications Protection.
Revoke access immediately, set expiration, disable forwarding, and watermark documents to maintain control of CUI.
Audit who has accessed CUI, when, where, and for how long.
Pre-configured DLP rules that scan emails and attachments to detect CUI, then automatically enforce encryption and access controls that are persist throughout supply chain workflows.
Learn how Cuick Trac can secure your CUI in less time, with less effort, and with more features than any other DFARS-compliant product on the market.
Cuick Trac, a solution by Beryllium InfoSec, is a FedRAMP Moderate Equivalent virtual enclave, known as the Cuick Trac Managed Enclave, designed for organizations that need to comply with NIST 800-171 and CMMC 2.0, Level 2.
Cuick Trac’s Managed Enclave has officially achieved FedRAMP Moderate Equivalency, reinforcing our commitment to secure, compliant, and scalable solutions for the Defense Industrial Base.
What this means for you:
Enhanced security & compliance for CUI protection requirements
Reduced burden for DFARS & CMMC compliance
A trusted, fully managed solution backed by FedRAMP-Recognized 3PAO attestation
Learn how this milestone benefits your organization!