The Federal Acquisition Regulation (FAR) has introduced a proposed rule to standardize the handling of Controlled Unclassified Information (CUI) across all federal agencies, not just the Department of Defense (DoD). This expansion presents significant opportunities for contractors and organizations working with federal agencies, reinforcing uniform security and compliance approaches for safeguarding CUI.
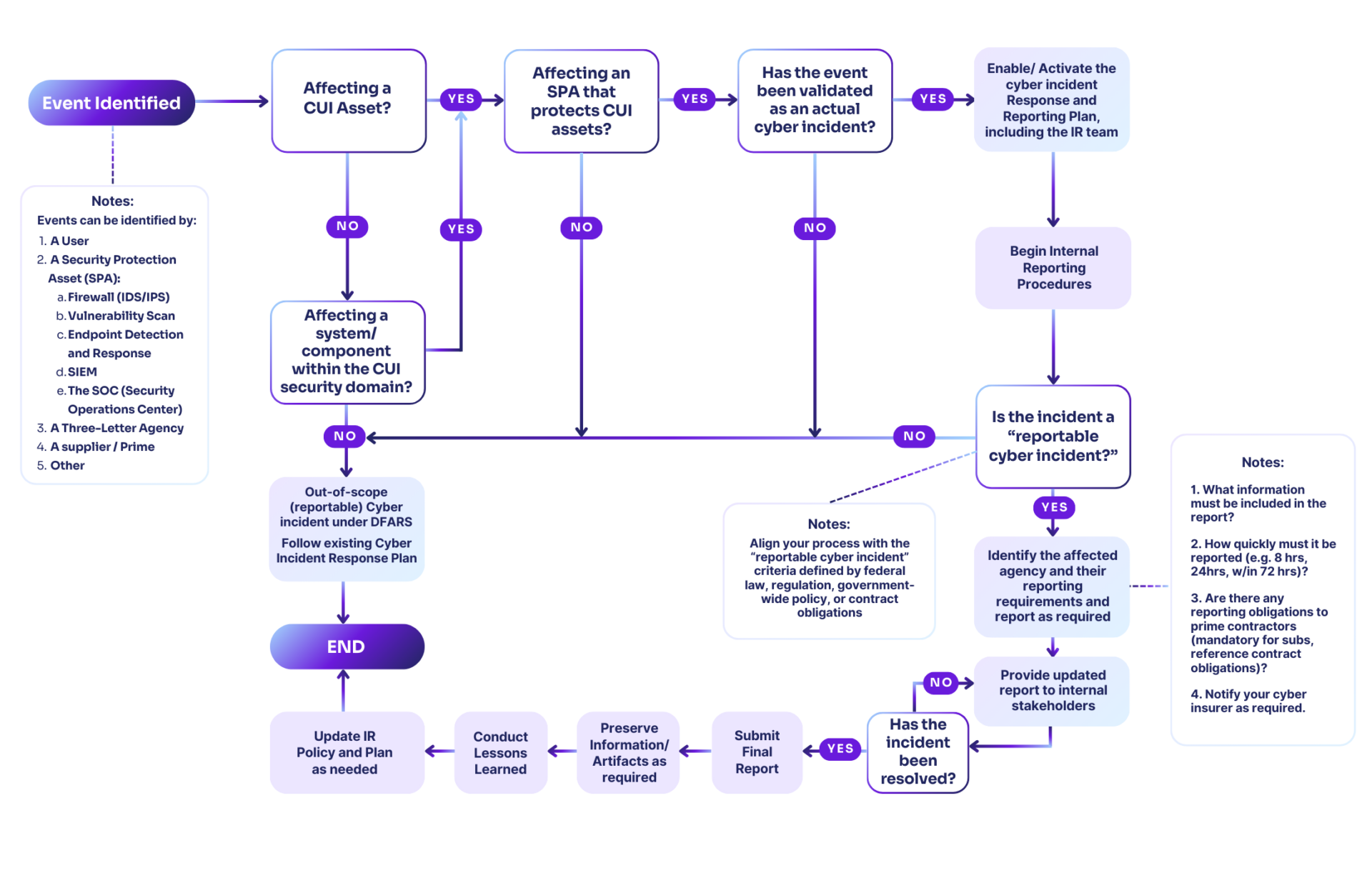
One of the most critical aspects of this proposed rule is the increased emphasis on incident response and reporting. Now referred to as CUI Incidents, these events trigger very demanding reporting timelines and evidence preservation requirements, reshaping how federal contractors must respond to “reportable cyber incidents” that may affect or affect CUI.
The proposed FAR CUI Rule mandates that contractors report any suspected or confirmed CUI incidents within eight (8) hours of discovery, a significant gas in the pedal acceleration from existing reporting timelines for DoD and DHS contractors. This aggressive reporting requirement aims to ensure the rapid containment and mitigation of potential threats to national security and thus reduce the potential damage from unauthorized access, use, disclosure, disruption, modification, or destruction of information/CUI.
Contractor Responsibilities Under the FAR CUI Rule
When a CUI Incident occurs, contractors must:
- Assess the impact – Determine what CUI was or could have been improperly accessed, used, processed, stored, disseminated, or disclosed.
- Construct a timeline – Track user activity and access methods to determine the scope of the breach.
- Report within 8 hours – Submit incident details to the agency website or designated point of contact (including using the DIBNet reporting format when applicable).
- Notify the Prime – Subcontractors must notify their prime contractors (or next higher-tier subcontractor) within the same eight-hour timeframe.
Beyond reporting, preserving evidence is critical. Contractors must protect system images and packet capture data for 90 days, ensuring that federal agencies have sufficient time to request forensic data for damage assessments.
Expanded Contractor Responsibilities: Reporting and Identifying CUI
The proposed rule introduces new FAR clauses that increase contractor responsibility in identifying and reporting potentially unmarked CUI:
- FAR 52.204-WW: Requires contractors to handle CUI during the solicitation phase and notify the government of any unmarked or mismarked CUI.
- FAR 52.204-XX: Establishes baseline CUI safeguarding requirements, reinforcing NIST SP 800-171 compliance.
- FAR 52.204-YY: Mandates contractors proactively report any information that could be CUI but lacks proper markings.
These provisions aim to create a more consistent and transparent approach to CUI across federal contracts, but they also increase contractor responsibility in helping agencies identify unmarked or misclassified information.
The Foundations for Compliance: What Federal Contractors Need to Know That the DIB Already Knows
For organizations already handling CUI under DoD contracts, many of these security expectations are familiar:
- Adequate Security & Compliance with NIST SP 800-171: The FAR CUI Rule aligns with the DoD’sDoD’s definition of “Adequate Security,” reinforcing that contractors must implement NIST SP 800-171 as a minimum standard for protecting CUI.
- Enhanced Security for High-Value Assets (HVA): Some organizations may need to comply with additional security requirements when a contract determines they are necessary to provide adequate security in dynamic environments. Contractors executing critical programs or handling HVAs and mission-critical CUI may also need to comply with the enhanced requirements outlined in NIST SP 800-172.
- CUI Specified Requirements: These include dissemination controls, limited distribution statements, expanded cyber incident reporting, and federal audit requirements.
Consistent Security Standards Drive Compliance Efficiency
One notable addition is the requirement that CUI will now be formally identified on the SF XXX, which will trigger security requirements under NIST SP 800-171. This reinforces the argument that similar to DFARS 7012, compliance with NIST 800-171 is mandatory whenever CUI is present in a federal contract.
One of the most significant challenges federal contractors may face under the proposed FAR CUI Rule is the potential misalignment of security requirements across different federal agencies. While CUI incident reporting can be addressed through policies and procedures and adherence to NIST SP 800-171 security requirements, the lack of consistency in which revision of NIST SP 800-171 is enforced could create substantial compliance burdens.
If federal agencies fail to align their security requirements and enforce different revisions of NIST SP 800-171, contractors may be forced to implement separate network architectures for different agencies—even though all agencies are handling the same sensitive data (CUI) with at least a moderate confidentiality impact.
Luckily, the proposed rule, as written, specifies NIST SP 800-171 Revision 2 (171r2). This is a critical step in ensuring alignment across agencies. However, to avoid future fragmentation, the final rule must not only retain this alignment but also include a clear plan for continuous synchronization as we transition through future revisions of NIST SP 800-171.
The bottom line is that the most effective path forward is for all federal agencies to enforce the same revision of NIST SP 800-171 at the time of contract award and throughout the contract’s lifecycle. This approach ensures that federal contractors can manage security requirements more efficiently without unnecessary and costly investments in multiple network architectures for different agencies.
A Shift in CUI Governance: More Accountability, More Transparency
The proposed FAR CUI Rule signals a shift towards a more structured and uniform approach to CUI governance across all federal agencies. While it introduces more structured compliance expectations, contractors who already adhere to NIST SP 800-171 will find themselves well-positioned to meet these new requirements.
However, the rule also underscores a broader responsibility for contractors—not just to protect CUI, but to identify it, classify it correctly, and report incidents more rapidly than ever before.
With stricter reporting timelines, enhanced evidence preservation obligations, and the potential for federal audits, organizations must adapt their cybersecurity programs to meet these new expectations.
For contractors working with the federal government, the message is clear: incident response and reporting is no longer just a cybersecurity best practice, it’sit’s a contractual obligation.
References: